With cyber threats on the rise and the increasing reliance on smartphones for storing personal data, securing your mobile device has never been more important.
We’ll walk you through the essential steps to safeguard your phone and secure your personal information. Let’s dive in!
On This Page:
- Strengthen Your Phone’s Security Settings
- Keep Your Operating System and Apps Updated
- Be Cautious with App Permissions and Downloads
- Be Mindful of Public Wi-Fi and Bluetooth Connections
- Utilize Mobile Security Apps
- Enable Two-Factor Authentication (2FA)
- Safeguard Your Data with Encryption and Backups
- Lock and Track Your Phone Remotely
- Recognize and Avoid Phishing Attempts
- Summary
- Frequently Asked Questions
Key Takeaways
- Strengthen your phone’s security settings using strong passcodes, biometric authentication, and adjusting privacy settings.
- Regularly update your operating system and applications.
- Be aware of phishing attempts, always know where your phone is, and use mobile security apps for protection against phone hacking.
Strengthen Your Phone’s Security Settings

The first line of defense against phone hacking is having bulletproof security settings. By using strong passcodes, utilizing biometric authentication, and adjusting privacy settings, you’ll be well on your way to securing your online accounts on mobile devices.
Remember, an ounce of prevention is worth a pound of cure.
Passcode Best Practices
A strong passcode is vital as it generates your phone’s encryption key, safeguarding your data.
For enhanced security, use a complex passcode with a mix of letters, numbers, and symbols. You can also use a strong password generator like this one to generate secure passwords.
Remember to periodically update your passwords to further protect your data from potential security breaches. To help you manage your various account passwords, use a password manager that offers apps for both mobile devices and desktops.
Biometric Authentication
Biometric authentication offers a more secure and convenient alternative to traditional methods like pattern unlocking. By utilizing unique biological characteristics such as fingerprints or facial recognition, biometric authentication provides a high degree of security.
Privacy Settings
Adjusting your phone’s privacy settings to limit app access to your sensitive data.
Android users should go to Settings > Privacy > Permission Manager and review each section to ensure that apps have appropriate access to your data and services.
For iOS-powered devices, go to Settings > Privacy & Security to review your privacy settings.
Keep Your Operating System and Apps Updated

Update your phone’s OS and apps regularly to address security vulnerabilities. Remember, as the saying goes, “A chain is only as strong as its weakest link.”
Automatic Updates
Enabling automatic updates keeps your device’s security measures up-to-date to ensure your device is always equipped with the most recent security measures and patches.
To enable automatic updates, navigate to your device’s settings and locate the option to enable automatic updates.
Some users claim that automatic updates can break their functionality, and while this is occasionally true, reduced functionality is better than a hacked phone.
App Management
Delete unused apps, as they require updates and can pose security risks.
By staying vigilant and removing outdated apps from your mobile device, you can keep it more secure and less vulnerable to hacking attempts.
Be Cautious with App Permissions and Downloads
Be cautious when downloading apps and granting permissions. A little caution goes a long way when it comes to securing your personal information.
Trusted App Sources
Obtaining apps from reliable sources guarantees the security of personal data and minimizes the possibility of malware and other potential risks. Stick to official app stores and avoid downloading apps from third-party websites or links.
By being cautious about where you download apps, you’ll reduce the likelihood of installing malicious apps on your device.
App Permissions
Review and limit app permissions to prevent unauthorized access to sensitive data. Be sure to assess the permissions requested by each app and make an informed decision before granting them. It’s always better to err on the side of caution when it comes to your personal information. This applies even stronger to allowing location data sharing.
Be Mindful of Public Wi-Fi and Bluetooth Connections

Using public Wi-Fi and Bluetooth connections can put your data at risk. To avoid phone hacking, always take precautions when connecting to public Wi-Fi networks and using Bluetooth devices.
Public Wi-Fi Precautions
When connecting to public Wi-Fi networks, using a Virtual Private Network (VPN) can provide added security. A VPN creates a safe and secure connection by encrypting your data. It also hides your IP address, stopping cybercriminals from intercepting or understanding your information.
Bluetooth Security
Turn off Bluetooth when not in use to prevent unauthorized access to your device. Bluetooth connections can be susceptible to malicious hacking, so be very selective about what devices and services you allow access to your phone.
Ensure that your Bluetooth is turned off when not in use, and be aware of the potential risks.
Utilize Mobile Security Apps

Mobile security apps, especially those combining antivirus and VPN, can effectively protect against threats.
Antivirus Solutions
Installing a reliable mobile antivirus solution (Bitdefender has a free solution) is a crucial step in preventing phone hacking. This is especially important for Android devices, which are more susceptible to phone hacking than iOS devices.
VPN Services
Using a VPN service, such as ExpressVPN or NordVPN, can help encrypt your internet traffic and protect your privacy. By encrypting your data, a VPN makes it more challenging for hackers to trace your online activities or intercept your sensitive information.
It’s an essential tool for maintaining your privacy and security in the digital age.
Enable Two-Factor Authentication (2FA)

Enabling two-factor authentication (2FA) provides an additional layer of security for your accounts on mobile devices. Requiring two forms of identification makes it more difficult for unauthorized individuals to gain access to your accounts.
Software Token-Based 2FA
Utilizing software token-based 2FA, such as Google Authenticator, offers better protection than SMS-based 2FA. Software token-based 2FA generates a one-time passcode (OTP) that the user submits along with their username and password to verify their identity.
Avoiding SMS-Based 2FA
Although SMS-based 2FA provides a layer of security, it is susceptible to attacks such as SIM swapping and phishing. To enhance the security of your accounts, opt for more secure alternatives such as authenticator apps or physical security keys for 2FA.
Safeguard Your Data with Encryption and Backups

Encrypting your data and taking regular backups is essential for protecting your personal information in case of a security breach, phone theft, device malfunction, or loss.
SD Card Encryption
Encrypting your SD card is a reliable way to protect the data stored on it from unauthorized access. This ensures that the data cannot be accessed without the correct authentication, providing a reliable way to protect the information stored on it.
Regular Data Backups
Performing regular data backups to cloud storage or external devices is essential for ensuring that your data is safe in the event of a security breach, phone theft, device malfunction, or loss. It’s important to have a copy of your data in case you need to erase your device remotely.
Lock and Track Your Phone Remotely
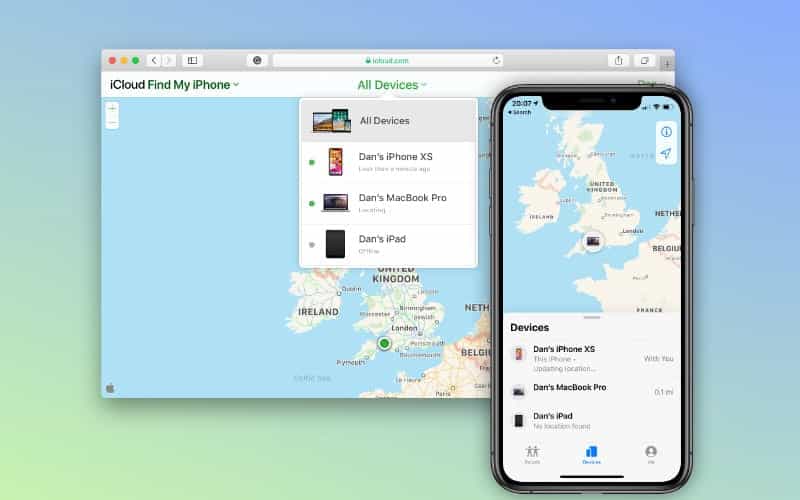
If your phone is lost or stolen, remote locking and tracking can protect your information and minimize damage.
Find My Device Services
Find My Device services are features provided by operating systems, such as Android and iOS, that enable users to locate, ring, lock, or erase their Android and iOS devices from a remote location. By using location-tracking features like Find My iPhone and Android’s Find My Device, you can locate your phone and take remote action to lock or erase it.
These services are incredibly useful for those who have lost their device or had it stolen.
Remote Wipe
Enabling remote wipe is a crucial security feature that allows you to erase data remotely from your device in case it’s lost or stolen. By erasing the device, you’ll prevent unauthorized access to your sensitive information and minimize the damage caused by a lost or stolen phone.
Recognize and Avoid Phishing Attempts

Phishing is a type of cyber attack that employs social engineering tactics to deceive individuals into divulging sensitive information, such as passwords, credit card numbers, and social security numbers.
Spotting Phishing Signs
Learning to spot phishing signs in emails, texts, and websites is extremely important for staying safe online. Be aware of suspicious sender addresses, generic greetings, pressing demands for action, and links to unfamiliar websites.
Knowing the signs of phishing will help you avoid falling victim to these malicious attacks.
Watch for Smishing & Vishing
Be cautious of smishing (SMS phishing) and vishing (voice phishing) attempts. These types of phishing attacks use text messages or phone calls to deceive individuals into providing personal information or money.
Always be cautious when receiving unsolicited messages or calls requesting sensitive information or financial transactions.
Beware of Juice Jacking
Juice jacking is a type of cyber attack where malicious software is installed, or data is stolen from a device when it’s charged using a public USB charging port. These ports, often found in airports, hotels, or public transportation hubs, can be compromised by hackers to access your personal data.
To guard against this, use a USB data blocker, often termed a “USB condom.” It allows charging without data transfer. Preferably, use your own cable and opt for traditional power outlets over public USB ports.
Reporting and Blocking
If you believe that you have been targeted by a phishing attempt, report it to the relevant company or website and block the sender or website to prevent further attempts. By reporting and blocking phishing attempts, you’ll help protect yourself and others from falling victim to these malicious attacks.
Taking the time to report and block phishing attempts is an important step in protecting yourself.
Maintain Physical Security
Maintaining physical security is just as important as protecting your phone from cyber threats. Keep your phone with you at all times, and consider using protective cases to prevent damage from drops or impacts.
Summary
In today’s digital world, securing your phone is crucial for personal and professional safety. By following the steps outlined in this guide, you’ll be well on your way to keeping your phone safe from potential threats, both online and offline.
Remember, protecting your mobile device is an ongoing process, so stay vigilant and keep your guard up to ensure your personal information remains secure.
Frequently Asked Questions
Can I stop my phone from being hacked?
You can take steps to protect against phone hacking, such as using a standalone VPN and antivirus app. Be sure to avoid suspicious websites and download only reputable apps to further protect yourself.
What are signs that your phone is hacked?
Unusual freezing, crashing, or restarting of your phone, strange activity on your other online accounts, and unexpected messages from unknown sources can all be signs that your phone has been hacked. It is important to be vigilant in spotting these signs.
Can hackers see through your phone?
Yes, hackers can potentially watch through your camera if they have installed spyware on your phone. Additionally, they could access any photos or videos previously taken on the device.



