With a heightened threat of cyber attacks, securing digital assets and sensitive data is paramount for businesses. The NIST Framework provides guidelines for managing cyber risks effectively.
This article unpacks the five core functions: Identify, Protect, Detect, Respond, and Recover, shedding light on the significance of the framework and how its implementation can be beneficial.
On This Page:
Understanding the Importance of Cybersecurity
The frequency and sophistication of cyber threats have significantly increased in recent years. Cybersecurity Ventures projects that the global cost of cybercrime will reach $10.5 trillion by 2025. These statistics underscore the need for businesses to reinforce their cyber defenses.
Malware, phishing scams, ransomware, and denial-of-service (DoS) attacks are prevalent forms of cyber threats. Cybersecurity isn’t limited to large corporations, but it’s also a pressing matter for small and medium-sized businesses.
The Rising Threat of Cyber Attacks

As digital landscapes continue to evolve, so too does the threat of cyber attacks. Criminals are developing increasingly sophisticated tactics to exploit vulnerabilities and access sensitive data. The projected global cost of cybercrime is set to reach an astronomical $10.5 trillion by 2025, according to Cybersecurity Ventures.
Different forms of cyber threats are being used to target unsuspecting victims. Malware, ransomware, and denial-of-service (DoS) attacks are prevalent, while phishing scams remain a major concern. Phishing has evolved into ‘smishing‘ (SMS phishing) and ‘vishing‘ (voice phishing), as cybercriminals exploit various communication channels to trick individuals into revealing personal information or downloading malicious software.
Whether you operate a small business or a multinational corporation, cybersecurity must be a top priority. Utilizing the framework core of the NIST Framework can be an effective part of a comprehensive cybersecurity program to manage these threats.
Why Businesses Need Cybersecurity Frameworks
Proactively securing assets against cyber threats is essential for businesses. One comprehensive guide for managing cybersecurity risk is the NIST Framework, developed by the National Institute of Standards and Technology.
This framework provides organizations with guidelines to understand and manage cyber risks, safeguard sensitive data, detect cybersecurity events, respond to cyber incidents, and restore normal operations post-attack. Let’s explore these key functions:
- Identify: It involves understanding cybersecurity risks to systems, assets, data, and capabilities. Asset management, risk assessment, and developing a risk management strategy are integral parts of this function. A well-managed asset management program identifies both physical and software assets, increasing organizational understanding.
- Protect: This function focuses on the implementation of safeguards to protect critical infrastructure services. Measures like access control, identity management, and data security protection are part of the protect function.
- Detect: It involves continuous monitoring of cybersecurity events, including intrusion detection and security event logging. Effective detection processes are vital in identifying potential cybersecurity incidents timely.
- Respond: This function aims to take action in response to a cybersecurity incident. It also involves coordinating with external organizational resources, such as law enforcement or cybersecurity incident response teams.
- Recover: It focuses on restoring normal operations post-cybersecurity incident. Recovery planning processes and the implementation of lessons learned are integral to this function.
By leveraging the NIST Framework, businesses can adopt a systematic and proactive approach to cybersecurity risk, ensuring the continuity of operations.
Introduction to NIST Cybersecurity Framework
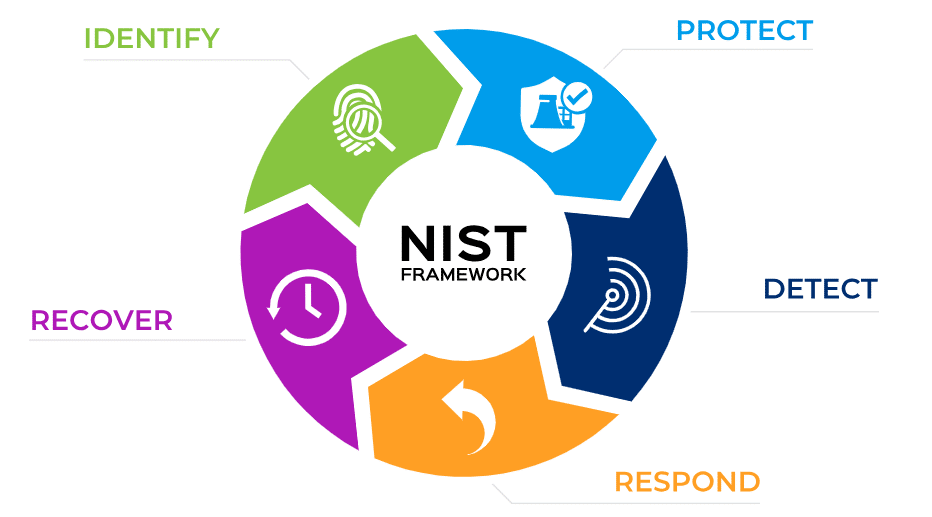
The NIST Framework is a set of voluntary guidelines, developed by the National Institute of Standards and Technology, for improving cybersecurity risk management. This framework offers a flexible and customizable approach to protect critical infrastructure.
Who Should Use the NIST Cybersecurity Framework?
The framework is applicable across sectors, including government agencies, financial institutions, healthcare providers, and manufacturing companies. Healthcare cybersecurity is particularly crucial as it involves sensitive patient data. Implementing the NIST Framework not only enhances security posture but also helps create a culture of cybersecurity awareness and resilience.
Detailed Overview of the Five Elements
The first element, Identify, revolves around understanding the cybersecurity environment. Recognizing potential cyber threats and assessing the potential impact of cyber threats is crucial to this function.
The Protect element focuses on implementing safeguards to prevent or minimize the impact of cyber attacks. Access controls, network security, data encryption, and reliable backup and recovery mechanisms are part of this function.
The Detect function emphasizes the importance of monitoring for cybersecurity events continuously. Timely identification enables forensic analysis and swift response to potential breaches.
The Respond element focuses on establishing an effective incident response program. This function entails developing response plans, detailing roles, and conducting regular response exercises.
The Recover function deals with the restoration of normal operations post-cybersecurity incident. The process involves data restoration, system reconfiguration, and security improvements.
Benefits of Implementing the NIST Framework
- Improved Risk Management: Implementing the NIST Framework leads to improved overall risk management by taking a proactive stance toward managing cybersecurity risk.
- Enhanced Communication and Understanding: The framework provides a common language and set of guidelines for internal and external communications about cybersecurity requirements.
- Compliance with Regulations: By following the NIST Framework, organizations can ensure compliance with industry-specific regulations and guidelines.
Practical Implementation of the NIST Framework
While the theoretical framework provides a valuable road map, its value truly emerges when put into practice. By following the framework core’s five key functions, organizations can implement an effective cybersecurity program that aligns with industry best practices and regulatory requirements.
Asset Management and Identifying Risks
An asset management program that includes both physical and software assets is crucial to the Identify function. Knowing what resources you have is the first step towards protecting them. The process should involve taking inventory of all assets, including devices, data repositories, and applications, and identifying their risk levels.
Simultaneously, an understanding of the organization’s risk strategy is essential. An effective risk management strategy should take into account the organization’s specific goals, constraints, risk tolerance, and the size and complexity of its operations.
Implementing Protective Measures
When it comes to the Protect function, data security protection and access control are vital. Implementing identity management measures that ensure only authorized individuals have access to certain information is a core aspect of cybersecurity. Additionally, organizations need to consider the protection of critical infrastructure services.
This function also requires the creation of an organizational understanding regarding the awareness of potential cybersecurity incidents and the response to them. In this regard, both internal and external communications play a significant role.
Detection and Response
The Detect function relies heavily on the ability to monitor cybersecurity events. Detection processes should be in place to identify potential issues swiftly. Responding to potential incidents also requires effective internal and external communications. Coordinating with external organizational resources can be integral to addressing and overcoming incidents.
Planning for Recovery
The Recover function involves planning processes that ensure the timely recovery of systems. Following an incident, swift action must be taken to restore normal operations. Importantly, recovery planning processes should not merely focus on immediate recovery but also on improving resilience in the face of future incidents.
Cybersecurity for Various Sectors
The NIST Framework is versatile and applicable across different sectors. Its principles can help secure critical infrastructure and operations in sectors like government, finance, and healthcare. With the rising significance of healthcare cybersecurity, the framework is increasingly seen as a crucial tool in this sector. Moreover, it offers valuable guidance on cybersecurity for small businesses that may lack the resources of larger corporations.
Conclusion
In conclusion, the NIST Framework is a robust approach to managing cybersecurity risk. Its five elements – Identify, Protect, Detect, Respond, and Recover – form the framework core, enabling businesses to strengthen resilience against cyber threats.



