Are you worried about the ever-increasing cyber threats? You’re not alone. As these threats continue to grow in sophistication, organizations need to be proactive in managing their cybersecurity risks. That’s where the NIST Cybersecurity Framework comes in.
This comprehensive guide will help you understand the framework and how it can benefit your organization, ensuring you stay ahead of the curve and protect your valuable assets.
On This Page:
Short Summary
- The NIST Cybersecurity Framework provides organizations with a structured approach to managing cyber risks, protecting essential infrastructure services, and restoring systems after an incident.
- Organizations need to assess their cyber risks, develop a framework profile and establish security controls based on the NIST Cybersecurity Framework Core Functions.
- Adhering to the standards provided by NIST can lead to improved risk management & compliance with legal requirements for increased security.
The NIST Cybersecurity Framework Explained
The NIST Cybersecurity Framework, developed by the National Institute of Standards and Technology (NIST), provides organizations with a set of guidelines and best practices to strengthen their cybersecurity posture and develop a risk management strategy. Since its publication in 2014, the framework has become a popular tool for organizations looking to make smart cybersecurity investments and decisions, focusing on cybersecurity risk management.
The benefits of using the NIST Cybersecurity Framework are numerous, such as helping organizations prioritize cybersecurity investments, assess the maturity of their program, and provide guidance on access control and other security measures. As cyber threats continue to evolve, the White House has urged agencies to improve the security of their systems by using more secure software and implementing continuous security monitoring practices, which the NIST Cybersecurity Framework can support.
Origin and Development
The NIST Cybersecurity Framework was created by the National Institute of Standards and Technology in response to the increasing cyber threats and the need for a standardized approach to cybersecurity. The framework was designed to assist both public and private organizations protect against cyberattacks and ensure data security.
As cyber threats continue to grow, the NIST Cybersecurity Framework remains a crucial tool for organizations looking to bolster their cybersecurity efforts and protect their valuable assets.
Key Components
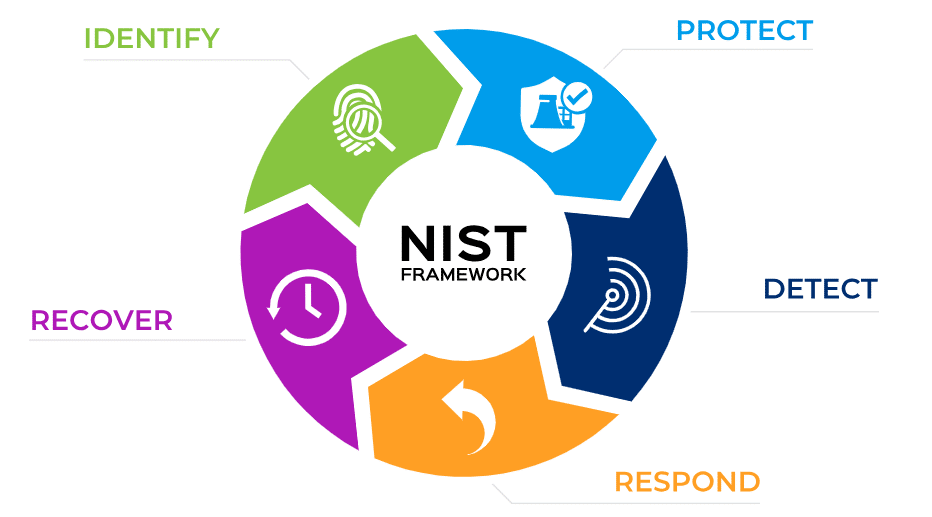
The NIST Cybersecurity Framework consists of three key components: the Core Functions, Implementation Tiers, and Profiles. These components help organizations develop a comprehensive cybersecurity program, tailored to their unique needs and requirements. The framework’s Core Functions are divided into five categories: Identify, Protect, Detect, Respond, and Recover, which provide a structured approach to managing cybersecurity risks.
The NIST Framework Implementation Tiers range from partial to adaptive and measure the maturity level of an organization’s cybersecurity program. By aligning their unique risks, assets, and compliance requirements with the NIST Framework Core Functions, organizations can create a tailored approach to managing their cybersecurity risks. This ensures that their cybersecurity measures are up to date and effective, helping to protect their critical infrastructure and sensitive data from cyber threats.
The 5 NIST Cybersecurity Framework Core Functions
The NIST Cybersecurity Framework is divided into Core Functions. These Functions are segregated into five distinct categories: Identify, Protect, Detect, Respond, and Recover. These functions provide a structured approach to managing cybersecurity risks, ensuring organizations can effectively address their unique threats and vulnerabilities.
By focusing on these core functions, organizations can develop a comprehensive and effective cybersecurity program that aligns with their business objectives and risk tolerances.
The main purpose of the NIST Cybersecurity Framework Core is to act as a bridge between multi-disciplinary teams, enabling them to communicate without understanding technical terms. This ensures that all organizational stakeholders can collaborate effectively, working together to meet their cybersecurity objectives and protect their critical systems from cyber threats.
Identify

The Identify function is crucial in helping organizations understand their cybersecurity risks and develop strategies to manage them, including identity management. By understanding the business context, the resources that support critical functions, and the related cybersecurity risks, organizations can create an organizational understanding to manage cybersecurity risk to systems, people, assets, data, and capabilities.
This function ensures that organizations prioritize and mitigate risks effectively, protecting their sensitive data and critical functions from potential cyber threats.
Protect

Protect function aims to secure essential infrastructure services by establishing protections and limiting the results of any possible cybersecurity event. This will help keep the services running without interruption. The key activities highlighted in this function include implementing technical security solutions to guarantee systems and assets are secure and resilient, monitoring and controlling access to systems and assets, and implementing suitable safeguards to ensure the availability of crucial infrastructure services.
By putting these protective measures in place, organizations can effectively safeguard against potential threats and vulnerabilities.
Detect

The Detect function emphasizes the importance of real-time monitoring and identifying cybersecurity events. Organizations can successfully detect security events and respond accordingly by staying up-to-date with accurate information.
This function also highlights the need to address shadow IT, which occurs when people use devices or software that aren’t approved by the network. Organizations can identify and address potential cybersecurity incidents by implementing effective monitoring and detection measures before they escalate.
Respond

The Respond function outlines how organizations should react to cybersecurity incidents to minimize their impact. This includes identifying the incident, containing it, eradicating it, and recovering from it. By having a well-defined response plan in place, organizations can effectively manage cybersecurity incidents and reduce the potential damage they may cause.
The Respond function ensures that organizations are prepared to handle any cybersecurity incidents that may arise and can take appropriate action to protect their critical systems and data.
Recover

The Recovery function focuses on restoring normal operations and improving resilience after a cybersecurity incident. Organizations can quickly restore any capabilities or services that were disrupted by the incident by creating and executing plans and processes to recover affected systems and assets.
This function also includes plans for maintaining resilience and restoring any capabilities or services disrupted by the incident. By focusing on recovery activities, organizations can effectively mitigate the impact of cybersecurity incidents and ensure their critical systems and data remain secure.
Implementing the NIST Cybersecurity Framework

Implementing the NIST Cybersecurity Framework involves assessing cyber risks, developing a framework profile, and establishing security controls to protect against threats. Organizations can tailor the framework to their unique requirements and ensure their cybersecurity measures are effective by understanding their specific risks, assets, and compliance needs.
Organizations need to align their risk assessment with the NIST Cybersecurity Framework Core Functions, allowing them to create a tailored approach to managing their cybersecurity risks. By following the guidelines and best practices outlined in the framework, organizations can effectively protect their critical infrastructure and sensitive data from cyber threats.
Assessing Cyber Risks
Assessing cyber risks involves understanding an organization’s unique risks, assets, and compliance requirements. Organizations can effectively prioritize and mitigate risks by identifying, analyzing, and evaluating potential threats and vulnerabilities to their information systems and data.
This risk assessment process is an essential part of the NIST Cybersecurity Framework, ensuring organizations comprehensively understand their cybersecurity risks and can take appropriate action to protect their systems and data.
Developing a Framework Profile
Developing a framework profile helps organizations align their risk assessment with the NIST Cybersecurity Framework Core Functions. By customizing the framework profile categories to suit their business objectives, organizations can create a tailored approach to managing their cybersecurity risks, ensuring that their cybersecurity measures are up-to-date and effective.
This allows organizations to focus on the most critical aspects of their cybersecurity program and prioritize the implementation of security controls to protect their assets and manage devices.
Establishing Security Controls
Establishing security controls involves implementing measures based on the NIST framework to protect assets and manage devices. By putting these protective measures in place, organizations can effectively safeguard their systems and data from unauthorized access, use, disclosure, disruption, modification, or destruction.
The NIST Cybersecurity Framework provides helpful guidelines and best practices for managing cybersecurity risk, including setting up security controls and ensuring organizations can effectively protect their critical infrastructure and sensitive data from cyber threats.
NIST Compliance and Its Importance

NIST compliance is essential for organizations to follow best practices and meet regulatory requirements. By adhering to the guidelines and standards set by the National Institute of Standards and Technology, organizations can effectively protect their systems and data from cyber threats, ensuring they remain secure and compliant with legal and regulatory requirements.
Compliance with NIST publications may be mandatory for federal agencies and government-affiliated entities, while voluntary for other organizations. Regardless of the type of organization, NIST compliance provides numerous benefits, including increased security, improved risk management, and a standardized approach to cybersecurity.
Mandatory vs. Voluntary Compliance
While compliance with NIST publications is mandatory for federal agencies and government-affiliated entities, it can be voluntary for other organizations. This distinction means that while some organizations are required to adhere to NIST guidelines and standards, others can choose to do so in order to improve their cybersecurity posture and meet industry best practices.
Regardless of whether compliance is mandatory or voluntary, adhering to NIST guidelines can help organizations effectively protect their systems and data from cyber threats and ensure they meet legal and regulatory requirements.
Benefits of Compliance
The benefits of NIST compliance are numerous, including increased security, improved risk management, and a standardized approach to cybersecurity. By adhering to the NIST Cybersecurity Framework, organizations can create a long-term approach to handling cybersecurity risks, recognizing potential threats, establishing the proper security measures, and regularly assessing the efficacy of those measures.
Additionally, NIST compliance can help organizations meet regulatory requirements and minimize the potential for legal issues arising from cybersecurity incidents, ensuring their security measures are up-to-date and effective.
Comparing NIST with Other Security Frameworks
Comparing NIST with other security frameworks, such as ISO 27001 and SOC 2, can help organizations determine the best approach to managing their cybersecurity risks. While each framework has its own focus, scope, and approach, they all share the common goal of helping organizations protect their systems and data from cyber threats.
| NIST | ISO 27001 | SOC 2 | |
|---|---|---|---|
| Origin | U.S. Government’s response to cybersecurity needs | International standard for Information Security Management Systems | Developed by AICPA, primarily for service providers storing customer data |
| Framework Core | Comprises Identify, Protect, Detect, Respond, Recover functions | Includes 14 domains with 114 controls for a complete Information Security Management System | Revolves around 5 Trust Service Principles: Security, Availability, Processing Integrity, Confidentiality, Privacy |
| Implementation | Voluntary, flexible, customizable to specific organizational needs | Requires formal certification, prescriptive requirements | Requires an audit, intended for more mature IT environments |
| Scope | Broad application, suitable for various sectors | All sectors, focuses more on data security | Ideal for service providers, underlines confidentiality and privacy of stored data |
| Compliance Visibility | Doesn’t offer a certification, less visibility to external parties | Internationally recognized certification | Audited report provides high visibility to clients, regulators |
Each framework has its own strengths and weaknesses, depending on the organization’s specific needs and requirements, as well as the expectations of internal and external stakeholders.
For example, while NIST is widely accepted and provides a comprehensive approach to cybersecurity, ISO 27001 focuses more on risk management and requires an external auditor to verify compliance.
On the other hand, SOC 2 is tailored to service providers and includes an audit from an external third party, ensuring that organizations meet specific security and privacy requirements.
NIST vs. ISO 27001
While both the NIST Cybersecurity Framework and ISO 27001 provide guidelines for managing cybersecurity risks, there are some critical differences between the two frameworks. ISO 27001 is an international standard focused on risk management and requires organizations to undergo an external audit to certify their compliance. This certification process can assure customers and partners that an organization is following best practices in information security.
In contrast, the NIST Cybersecurity Framework is a self-certification system that is widely accepted and provides a more comprehensive approach to cybersecurity, making it a popular choice for organizations looking to ensure their systems and data remain secure.
NIST vs. SOC 2
Both NIST and SOC 2 address information security controls, but they have different focuses and requirements regarding implementation and auditing. SOC 2 is part of the System and Organizational Controls framework and is more demanding regarding documentation and implementation, requiring an audit by an independent third party to verify compliance.
In contrast, NIST 800-53 is more flexible and allows organizations to tailor their security controls to their unique risk profile. However, implementing effectively requires a thorough understanding of the organization and its risks.
Ultimately, the choice between NIST and SOC 2 will depend on an organization’s specific needs and requirements and the industry and regulatory landscape in which they operate.
Tools and Resources for NIST Implementation
Various tools and resources are available to help organizations implement the NIST Cybersecurity Framework, ensuring they follow best practices and meet regulatory requirements. By leveraging these resources, organizations can effectively manage their cybersecurity risks and protect their valuable assets from cyber threats.
NIST publications provide detailed guidance on specific aspects of cybersecurity, such as NIST 800-53 and 800-171, which outline the necessary controls and requirements for federal information systems and contractors handling controlled unclassified information (CUI).
Additionally, risk management guides, such as the NIST Risk Management Framework, can help organizations develop a comprehensive cybersecurity plan, ensuring their systems and data remain secure and protected from cyber threats.
NIST Publications
NIST publications, such as NIST 800-53 and 800-171, provide organizations with detailed guidance on specific cybersecurity aspects, helping them design, implement, and operate the necessary controls to protect their systems and data. These publications cover a wide range of topics, including establishing and managing information security programs, security controls, risk management advice, and technical details.
By leveraging these publications, organizations can ensure they follow best practices and meet regulatory requirements, protecting their critical infrastructure and sensitive data from cyber threats.
Risk Management Guides
Risk management guides, such as the NIST Risk Management Framework, can help organizations develop a comprehensive cybersecurity plan, ensuring their systems and data remain secure and protected from cyber threats.
These guides provide detailed instructions on using the NIST Cybersecurity Framework to assess and manage cybersecurity risks, aligning organizational requirements and objectives with the desired outcomes provided in the framework core.
Summary
In conclusion, the NIST Cybersecurity Framework is an essential tool for organizations looking to effectively manage their cybersecurity risks and protect their valuable assets from cyber threats. By following the guidelines and best practices outlined in the framework, organizations can develop a comprehensive and effective cybersecurity program that aligns with their business objectives and risk tolerances.
With a wide range of tools and resources available, such as NIST publications and risk management guides, organizations can confidently implement the NIST Cybersecurity Framework and ensure they meet regulatory requirements and industry best practices.
Frequently Asked Questions
What are the five functions of the NIST Cybersecurity Framework?
The NIST Cybersecurity Framework consists of five core functions: Identify, Protect, Detect, Respond, and Recover. These functions provide activities, desired outcomes, and applicable references to help secure critical infrastructure sectors.
In which sectors can the NIST Cybersecurity Framework be used?
The NIST Cybersecurity Framework finds utility across a vast range of sectors, due to its adaptability and comprehensive approach to managing cybersecurity risk. It’s extensively employed in healthcare cybersecurity for safeguarding patient data and systems, in finance to secure sensitive financial data and infrastructure, and in education to protect student records and research data. The retail and manufacturing sectors use it to protect customer data, payment systems, intellectual property, and supply chain data.
Government agencies apply the framework to ensure the security of public services and sensitive data. Energy sectors use it to safeguard critical infrastructure like power plants and grid systems. IT, telecommunications, and especially small businesses, which often lack the extensive resources of larger organizations, also benefit from the framework’s flexible and cost-effective strategies for managing cybersecurity risk.
What is the difference between ISO 27001 and NIST?
ISO 27001 focuses on risk-based management and is best suited for organizations that have reached operational maturity, while NIST CSF is more technical and better for the initial stages of a cybersecurity risk program.
What is the difference between NIST 800 171 and 800-53?
NIST 800-171 applies to non-federal systems and organizations, while NIST 800-53 is specific to federal organizations. They both have to do with protecting data security, but NIST 800-171 is focused more on handling personal information and other sensitive data.
What is the purpose of the NIST Cybersecurity Framework?
The NIST Cybersecurity Framework helps organizations strengthen their cybersecurity posture and develop a risk management strategy, providing guidance and best practices to achieve this.
It offers a comprehensive approach to managing cybersecurity risk, from identifying and assessing risks to responding to incidents and recovering from them. It also provides a common language for organizations to communicate about cybersecurity risks and collaborate on solutions.



