Endpoint Detection and Response (EDR) has emerged as a game-changing cybersecurity solution that empowers organizations to avoid cyber threats. But what exactly is EDR? How does it work? And what sets it apart from traditional endpoint security solutions?
This article will explore the ins and outs of endpoint detection and response, its evolution, and how it can be integrated with other security tools to create a comprehensive defense against cyberattacks.
On This Page:
- Key Takeaways
- Understanding EDR: A Comprehensive Overview
- The Evolution of EDR Technology
- Key Components of an Effective EDR Solution
- How EDR Works: From Detection to Remediation
- EDR vs. Traditional Endpoint Security Solutions
- The Role of Threat Intelligence in EDR
- EDR and Machine Learning: A Powerful Combination
- Managed EDR Services: Outsourcing for Enhanced Protection
- EDR in Diverse Environments: Cloud and IoT
- Compliance and Regulations: How EDR Helps
- Integrating EDR with Other Security Tools
- Real-Life EDR Success Stories
- The 4 Best Industry-Leading EDR Providers
- Endpoint Protection Platforms (EPP) vs. Endpoint Detection and Response (EDR)
- Conclusion
- Frequently Asked Questions
Key Takeaways
- EDR is a comprehensive cybersecurity solution for monitoring end-user devices, detecting and investigating threats, and providing rapid response capabilities.
- EDR provides organizations with a more proactive approach to protection against cyberattacks than traditional endpoint security solutions.
- Managed EDR Services offer access to experienced professionals and comprehensive security solutions for enhanced protection in diverse environments such as cloud, IoT, or BYOD.
Understanding EDR: A Comprehensive Overview

Endpoint Detection and Response (EDR) is a cybersecurity solution designed to:
- Monitor end-user devices for potential malicious activities and manage endpoint data
- Provide detection, investigation, and response capabilities to protect against cyber threats
- Rapidly identify and counteract successful endpoint attacks within a comprehensive endpoint security framework, including antivirus capabilities.
The increased adoption of EDR is driven by the expanding number of network-connected endpoints and the growing sophistication of cyberattacks. EDR solutions aid security teams in detecting endpoint threats, mitigating security incidents, and analyzing these incidents to prevent future recurrences.
Potential threats are communicated to security personnel through the product interface or via integration with threat intelligence services or a ticketing system.
The Evolution of EDR Technology
Endpoint Detection and Response technology first appeared in 2013 to facilitate forensic investigations that required intricate endpoint telemetry to scrutinize malware and comprehend precisely what an attacker did to a compromised device. The term “EDR” was initially introduced by Anton Chuvakin from Gartner in 2013 and was later abbreviated to EDR in 2015.
Since its inception, EDR technology has shifted its focus from forensic investigations to providing advanced response endpoint detection and antivirus capabilities. EDR’s evolution has rendered it a vital tool in the cybersecurity landscape, offering a more holistic and proactive approach to endpoint security and safeguarding devices from a range of cyber threats.
Key Components of an Effective EDR Solution
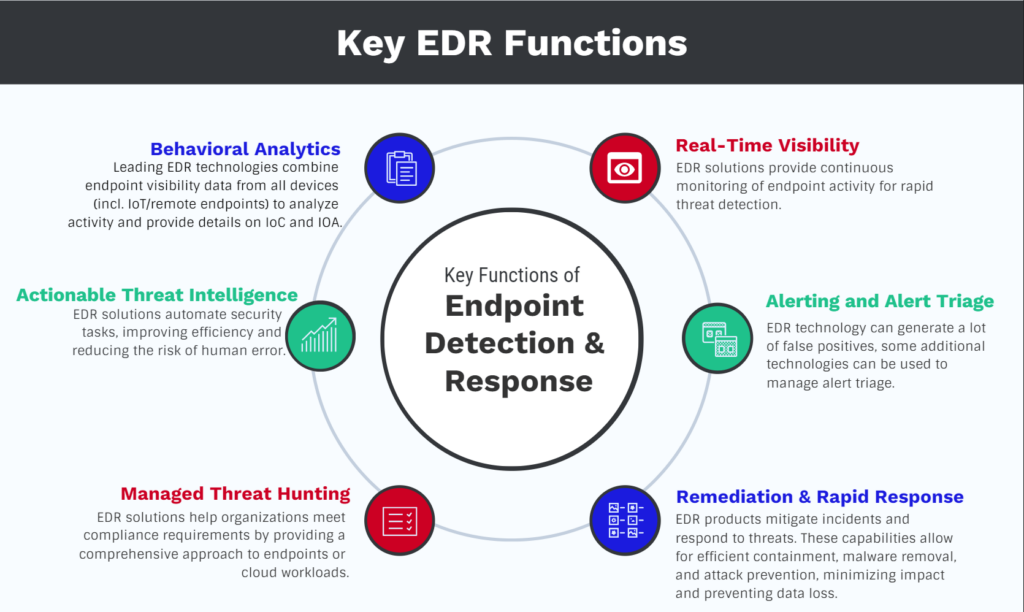
An effective EDR solution comprises several essential elements, including:
- Endpoint visibility
- A threat database
- Behavioral protection
- Insight and intelligence
- Rapid response
- Cloud-based architecture
EDR solutions provide enhanced visibility into endpoint activities by capturing granular activity and detecting potentially malicious behavior.
A threat database is crucial for effective EDR implementation, enabling the extraction of telemetry data to identify potential attacks. Behavioral protection is a critical component of EDR, aiding in detecting suspicious activities before a breach occurs. An EDR solution can be pre-configured with rules that can detect when incoming data signals a known type of security breach and then trigger an automated response.
A user-friendly admin console is a vital part of EDR solutions, providing admins with a holistic view of their endpoints’ security and the ability to generate reports for further investigation. Ensuring the admin console is readily accessible is essential so that security personnel can access threat data and implement remedial measures from any location at any time.
Related:
Best Antivirus Solutions for Medium and Large Businesses
How EDR Works: From Detection to Remediation
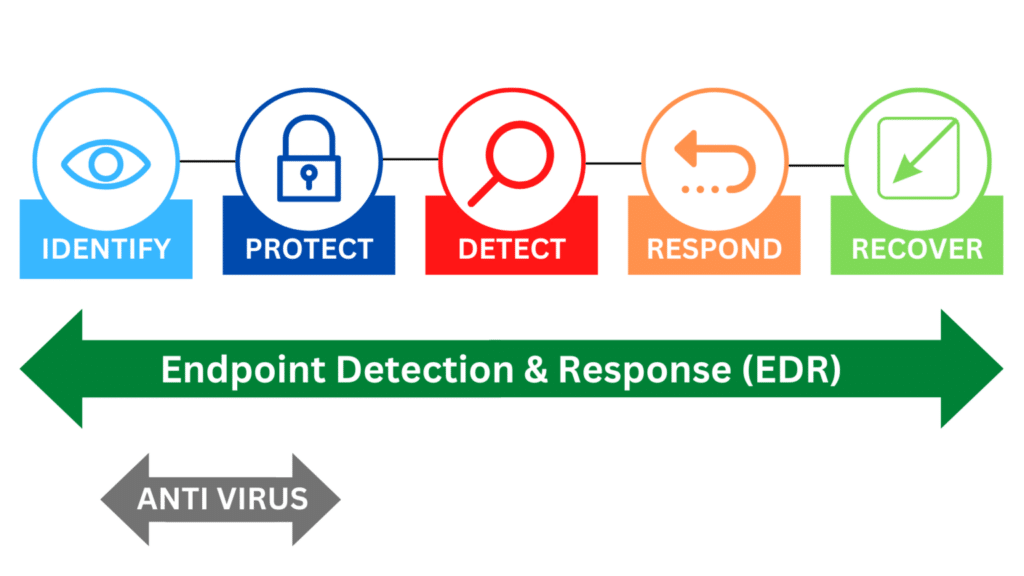
Endpoint Detection and Response (EDR) functions by continually monitoring endpoint activities, evaluating events, generating notifications, and providing automated or guided remediation to reduce the impact of cyber attacks. EDR is adept at collecting and analyzing data to identify potential attacks, thereby increasing visibility into systems and alerting when something appears abnormal.
EDR tools offer a thorough analysis of a wide range of events, covering everything from:
- standard laptops and desktop PCs
- mobile devices
- servers
- IoT
- cloud workloads
This helps identify any potential suspicious activity. These tools generate alerts to aid security analysts in uncovering, investigating, and remediating any issues. EDR tools gather telemetry data on any dubious activity. This data can be enhanced even more with additional contextual information gained from connected events.
A timely response in EDR can prevent an attack from escalating into a breach, enabling organizations to resume operations swiftly.
EDR vs. Traditional Endpoint Security Solutions

The primary purpose of EDR is to:
- Allow security teams to gain deeper insights into potential threats
- Automatically contain and eliminate threats
- Offer a more proactive approach to mitigating threats and preventing repeat attacks before they spread
Traditional endpoint security solutions focused mainly on preventive measures, which compromised detection and response capabilities, leaving endpoints vulnerable to attacks once the outer defenses were breached.
As a result, an integrated endpoint security solution that balances prevention, endpoint threat detection, and response is essential for comprehensive protection, and a security team plays a vital role in ensuring this balance.
EDR, on the other hand, enables organizations to:
- Identify and address threats that circumvent traditional defenses
- Provide more comprehensive protection against cyberattacks
- Enhance their overall cybersecurity posture
- Reduce the risk of breaches
By integrating EDR security with existing security tools and infrastructure, we can describe emerging security systems effectively, utilizing EDR security solutions.
Related: EDR vs. XDR vs. MDR: Comparing Detection & Response Solutions
The Role of Threat Intelligence in EDR
Threat intelligence significantly contributes to EDR by providing crucial context about advanced threats and adversaries, which enhances detection and response capabilities. One comprehensive knowledgebase and framework based on the analysis of millions of actual cyberattacks is the Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) project.
ATT&CK is a comprehensive approach to categorizing cyber threats. It looks at the tactics and system vulnerabilities exploited, malware tools used, and criminal groups associated with the attack.
Threat intelligence facilitates the detection and analysis of threats through leveraging large-scale data, machine learning capabilities, and advanced file analysis. This enables EDR solutions to identify sophisticated cyberattacks, unseen malware, and security breaches in real time, thereby allowing for a timely response to potential threats.
EDR and Machine Learning: A Powerful Combination

EDR can utilize machine learning to automate specific investigative steps and learn an organization’s typical behaviors, thereby enhancing threat detection and response. By using machine learning and artificial intelligence, EDR solutions can automate investigations and adjust to the distinct behavior of an organization, thereby enhancing threat detection and response.
EDR employs machine learning algorithms for continuous endpoint activity monitoring and suspicious behavior identification. Machine learning is used to detect atypical patterns in user behavior, thereby enhancing threat detection capabilities. Additionally, it leverages large-scale data and advanced file analysis to detect threats effectively.
Managed EDR Services: Outsourcing for Enhanced Protection
Organizations now have the ability to outsource their Managed Endpoint Detection and Response (EDR) capabilities to experienced cybersecurity providers. This provides them with increased security and compliance measures. By collaborating with a managed EDR service, organizations can gain access to the knowledge and resources of experienced professionals devoted to detecting, monitoring, and responding to threats on their endpoints.
Managed EDR services provide a comprehensive security solution. It offers ongoing monitoring of endpoints, proactive threat hunting, and immediate incident response.
The primary difference between Managed EDR and traditional EDR solutions is the introduction of human expertise. Managed EDR offers guided remediation, actionable insights, and single-click fixes, while traditional EDR solutions detect suspicious activity and require either automation or manual intervention for triaging.
EDR in Diverse Environments: Cloud and IoT
Enhanced endpoint security capabilities are provided by Extended Detection and Response (EDR) for cloud environments. It helps to protect cloud-based endpoints like virtual machines (VMs) and containers. Cloud-based EDR solutions offer a range of features specifically designed to address the particular security needs of endpoints in cloud environments. A cloud-based EDR solution enables precise, real-time search, analysis, and investigation without affecting endpoints.
In addition to cloud environments, EDR can also be tailored to protect Internet of Things (IoT) devices and Bring Your Own Device (BYOD) environments. By adapting EDR solutions to secure diverse environments, organizations can ensure comprehensive security coverage across their entire network.
Compliance and Regulations: How EDR Helps
EDR solutions enable organizations to fulfill and sustain adherence to applicable regulations, including GDPR, HIPAA, and PCI DSS. EDR assists with compliance by providing real-time insight into endpoint activities, detecting threats, and providing reporting capabilities to fulfill regulatory requirements. It also enables organizations to detect and respond to security incidents on individual devices, thus helping to satisfy regulations.
Implementing EDR solutions offers several benefits for organizations.
- Boosts overall cybersecurity posture
- Helps comply with constantly evolving regulatory requirements
- Highlights commitment to data protection and security best practices.
Integrating EDR with Other Security Tools

The integration of EDR and SOAR (Security Orchestration, Automation, and Response) platforms can provide the following benefits:
- Streamline workflows
- Speed up response times
- Foster productive collaboration among security teams
- Enhance incident response capabilities
- Increase visibility and detection
- Optimize security operations
- Reinforce threat response planning
By integrating EDR with other security solutions like SOAR, organizations can:
- Streamline their incident response processes
- Improve collaboration across security teams
- Enhance an organization’s overall cybersecurity posture
- Ensure a more robust defense against cyber threats.
Real-Life EDR Success Stories
Real-world EDR success stories underscore the effectiveness of EDR in identifying and mitigating cyber threats, safeguarding organizations from potential breaches and associated financial losses.
For example, CrowdStrike’s Falcon platform has received high praise from customers for its value and effectiveness in protecting their endpoints. CCSiNET conducted reviews of three case studies of organizations that implemented modern endpoint protection solutions, showcasing the impact of EDR in their security operations.
Other success stories include AT&T’s Stories from the SOC blog series, which provide detailed accounts of real-world security incident investigations, and Todyl’s penetration test utilizing EDR and Next-Generation Antivirus (NGAV) to protect Genuine Technology Group.
These success stories highlight the importance and effectiveness of EDR solutions in today’s complex cybersecurity landscape.
The 4 Best Industry-Leading EDR Providers
1. CrowdStrike Falcon
Known as one of the best EDR security solutions on the market with advanced endpoint threat detection and response, AI integration, and a robust cloud solution.
- Key Features: Real-time threat detection, AI-driven analysis, cloud-native architecture.
- Best For: Organizations looking for a scalable, cloud-native solution.
- User Reviews: Highly praised for its ease of use and effective threat detection.
2. SentinelOne
Known for its AI-driven technology and strong threat detection capabilities.
- Key Features: Behavioral AI technology, automated responses, and full visibility across the network.
- Best For: Businesses that want a proactive, AI-driven approach to endpoint security.
- User Reviews: Known for its robust detection capabilities and low false positives.
3. Carbon Black (VMware)
Offers comprehensive endpoint security with cloud-native architecture.
- Key Features: Cloud-native endpoint protection, customizable scripting, and threat hunting.
- Best For: Enterprises needing a flexible, customizable solution.
- User Reviews: Users appreciate the granular control and comprehensive reporting.
4. Sophos Intercept X
Popular for its deep learning technology and exploit prevention.
- Key Features: Deep learning technology, exploit prevention, and ransomware protection.
- Best For: Small to medium-sized businesses looking for robust, easy-to-manage security.
- User Reviews: Lauded for its user-friendly interface and effective exploit prevention.
Endpoint Protection Platforms (EPP) vs. Endpoint Detection and Response (EDR)
Both EPP and EDR serve crucial roles in endpoint security, but they address different aspects.
EPP is more about prevention and is generally easier to manage, making it suitable for businesses that want basic, effective security. EDR, on the other hand, is about deep analysis and response, ideal for businesses that are targeted frequently and are willing to invest in more advanced security measures.
Often, you’ll find solutions that combine both EPP and EDR for comprehensive endpoint security.
Endpoint Protection Platforms (EPP)
- Purpose: Primarily focused on prevention.
- Features: Includes antivirus, firewall, and intrusion prevention systems.
- Scope: Aims to stop threats before they infiltrate the network.
- Management: Typically managed through a centralized console.
- User Interaction: Generally requires less user interaction once set up.
- Best For: Businesses that want a set-it-and-forget-it solution for basic security needs.
Endpoint Detection and Response (EDR)
- Purpose: Focused on detection, analysis, and response to threats.
- Features: Includes threat hunting, behavioral analytics, and detailed data recording.
- Scope: Aims to detect and investigate suspicious activities on endpoints for further analysis.
- Management: Often requires a more hands-on approach for monitoring.
- User Interaction: May require specialized skills for threat analysis and response.
- Best For: Businesses that need advanced threat detection and are willing to invest in specialized skills or services.
Conclusion
Endpoint Detection and Response (EDR) has emerged as a powerful and proactive cybersecurity solution that helps organizations detect and remediate cyber threats. Organizations can enhance their overall cybersecurity posture and comply with necessary regulations by understanding EDR’s evolution, key components, and integration with other security tools like SOAR.
Real-life EDR success stories further demonstrate the value and effectiveness of EDR solutions in protecting organizations from potential breaches and financial losses. Embrace the power of EDR and safeguard your organization’s endpoints against today’s ever-evolving cyber threats.
Frequently Asked Questions
How does machine learning enhance EDR capabilities?
Machine learning significantly enhances EDR capabilities by making the system smarter, faster, and more adaptable. It allows for a more proactive approach to security, capable of identifying and responding to threats that traditional methods might miss. For medium to large businesses that face a variety of evolving threats, integrating machine learning into their EDR systems can offer a more robust and responsive security posture.
What benefits do Managed EDR services provide?
Managed EDR services offer a comprehensive, hands-off approach to endpoint security, making them an excellent option for medium to large businesses that may not have the resources for a dedicated in-house team. They combine expertise, continuous monitoring, and advanced technologies to provide robust security with the added benefits of cost-effectiveness and scalability.